Summary
Biometrics has emerged as one of the most powerful tools in modern cybersecurity. From unlocking your smartphone to verifying your identity at the airport, biometrics has redefined what digital security means in today’s hyper-connected world. But what exactly are biometrics? How does biometric authentication work? And how secure is it really?
In this comprehensive guide, we’ll explore what biometrics are, how they’re used in security systems, their benefits, risks, and the future of this advanced technology.
Security has always been about one simple principle — proving who you are.
Traditionally, this was done with passwords, PINs, or ID cards. But passwords can be forgotten, lost, or stolen. That’s where biometrics in security enters the picture.
Biometrics uses your unique biological and behavioral traits to verify your identity. From fingerprints and facial scans to voice patterns and iris recognition, biometric systems are replacing traditional methods due to their accuracy and convenience.
Today, biometric authentication is used in smartphones, banks, offices, government IDs, and even cars. But with this convenience comes a growing debate about privacy, data storage, and potential misuse.
Before exploring those concerns, let’s begin with the basics — what biometrics actually means.
What is Biometrics?

In simple terms, biometrics refers to biological measurements or physical characteristics that can be used to identify a person.
These characteristics are unique to every individual — no two people share the same fingerprint, retina pattern, or even the same way of speaking.
Biometrics bridges the physical and digital worlds by turning your biological identity into digital data that security systems can read and analyze.
For example:
- Your fingerprint is scanned and converted into a mathematical template.
- That template is stored securely.
- When you try to unlock your phone, the system compares your new fingerprint scan to the stored template.
- If it matches, you’re granted access.
In essence, biometrics answers the question:
“Can we identify who you are using your biological and behavioral features?”
What is Biometric Data
Biometric data refers to the digital representation of your physical or behavioral traits that are used for identification or verification.
There are two main types of biometric identifiers:
1. Physical identifiers
These include measurable biological characteristics such as:
- Fingerprints
- Facial structure
- Iris and retina patterns
- Hand geometry
- DNA
2. Behavioral identifiers
These are patterns in the way you act, such as:
- Typing speed and rhythm
- Voice pitch and tone
- Walking style (gait)
- Mouse movement patterns
How biometric data is used:
- A sensor captures your biometric sample (e.g., a fingerprint or voice).
- The data is converted into a digital template using algorithms.
- The template is encrypted and stored securely on the device or a server.
- During verification, new samples are matched against stored templates to confirm identity.
This process makes biometric authentication both personalized and efficient.
Types of Biometrics in Security
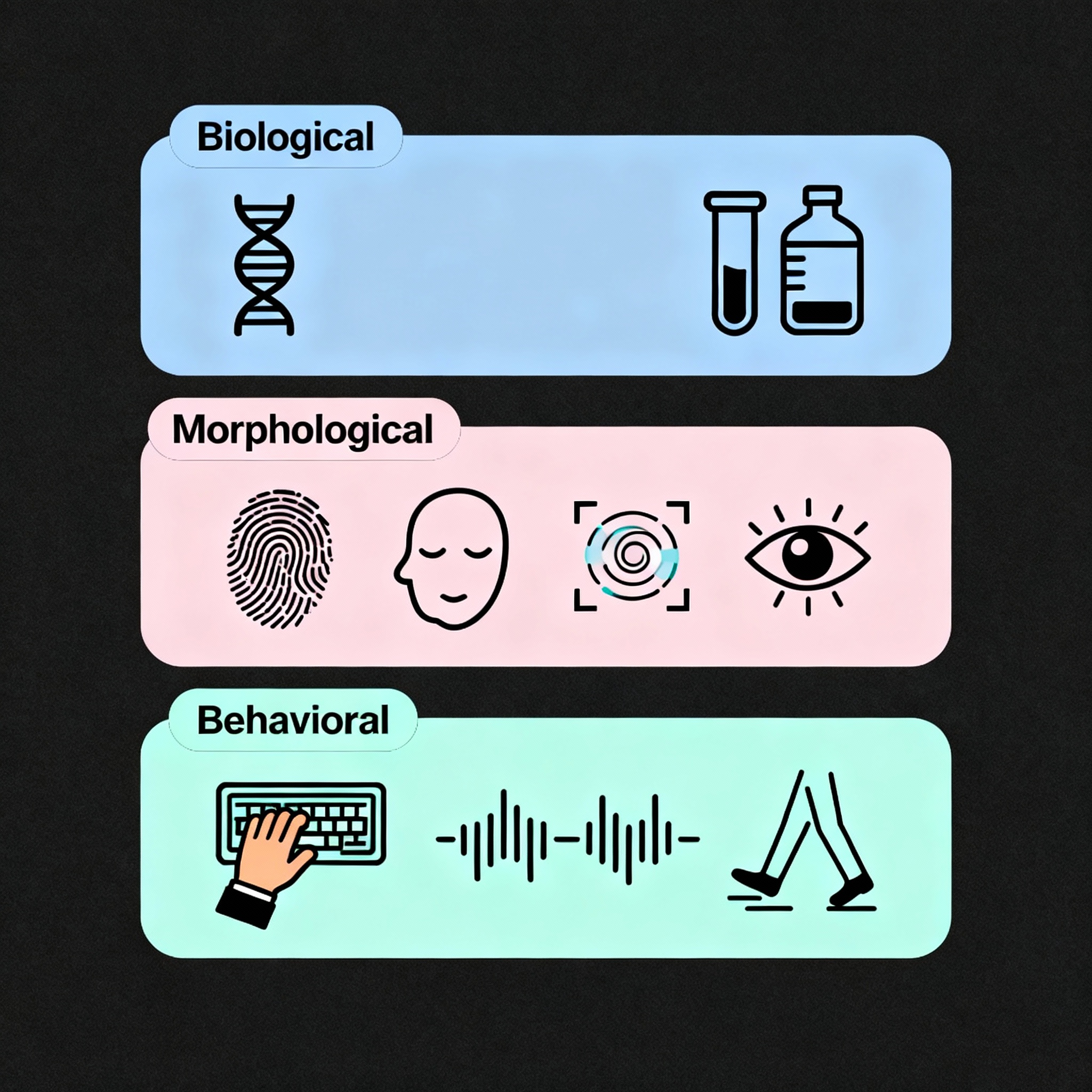
Biometrics can be broadly divided into three categories, based on what aspect of the person is being measured.
A. Biological Biometrics
These use genetic or molecular traits for identification.
Examples include:
- DNA profiling
- Blood or tissue analysis
They’re mostly used in forensic investigations and medical research rather than everyday access systems because they require laboratory testing.
B. Morphological Biometrics
This category involves physical structures of the body that can be mapped or scanned digitally.
Examples include:
- Fingerprints
- Facial features
- Eye scans (iris or retina)
Applications:
- Unlocking smartphones
- Security access in corporate offices
- Border control (e-passports and immigration checks)
Morphological biometrics are among the most common forms of biometric security in consumer and enterprise use.
C. Behavioral Biometrics
These depend on the unique ways in which a person behaves.
Examples include:
- The way you type or sign your name
- The tone and rhythm of your speech
- How you move your mouse or walk
Behavioral biometrics are particularly useful in fraud detection systems, as they can continuously monitor user behavior even after login.
5. How Biometric Security Works

Let’s break down how biometric authentication works step-by-step:
- Capture: A biometric scanner or sensor collects your data (fingerprint, face scan, etc.).
- Conversion: The system converts this raw data into a digital template.
- Storage: The encrypted template is stored on your device or in a secure server.
- Matching: When you try to access a system, your new biometric input is compared to the stored template.
- Authentication: If it matches, access is granted.
This process is faster and more reliable than password verification.
In most smartphones, biometric data never leaves the device — it is stored locally in a secure enclave.
In short, your body becomes the key to unlock your data and devices.
Examples of Biometric Security in Everyday Life
Biometric technology is already a part of daily life — often without us even realizing it.
Some practical examples include:
- Smartphones: Face ID and fingerprint sensors are the most common forms of biometric authentication used today.
- Banking: Citibank uses voice recognition for secure account access, while other financial institutions use fingerprint or facial verification for app logins.
- Automobiles: Companies like Ford have explored using biometric sensors in cars to recognize drivers by their heartbeat or face.
- Travel: E-passports include chips containing biometric data like facial photos or fingerprints, ensuring faster and safer immigration processing.
- Government IDs: India’s Aadhaar system uses iris scans, fingerprints, and facial data to authenticate over a billion citizens.
These examples demonstrate that biometrics in security have become an essential part of both personal convenience and national infrastructure.
Advantages of Using Biometrics in Security
Biometric authentication offers several key advantages over traditional password-based systems.
1. Convenience
You don’t have to remember passwords or carry ID cards — your biometric identity is always with you.
2. Security
Since biometric data is unique, it’s extremely difficult to forge, steal, or replicate.
3. Speed
Biometric authentication provides near-instant verification. Unlocking your phone or accessing an office door takes just seconds.
4. Accuracy
Modern biometric systems have high accuracy rates, often exceeding 99% in controlled environments.
5. Integration
Biometric security can be combined with other systems like smart locks, payment gateways, or two-factor authentication for added protection.
Limitations and Risks of Biometric Security
Despite its advantages, biometric security also comes with challenges that cannot be ignored.
1. Privacy Concerns
Biometric systems can collect data without user consent — for example, facial recognition cameras in public areas. This raises questions about surveillance and data misuse.
2. Data Breaches
Biometric databases are valuable targets for hackers. If stolen, unlike passwords, biometrics cannot be changed.
A real-world example:
In 2015, the U.S. Office of Personnel Management was hacked, and the fingerprints of over 5 million employees were stolen — a permanent compromise of their biometric identity.
3. Spoofing
Hackers have demonstrated that it’s possible to fool some biometric systems.
For instance, 3D models made from social media photos have successfully bypassed facial recognition systems in lab tests.
4. Permanency Problem
You can reset a password, but you can’t reset your fingerprint or iris. Once compromised, your biometric data remains vulnerable indefinitely.
Security Enhancements and Anti-Spoofing Techniques
To combat these challenges, researchers and companies are continuously improving biometric technology.
A. Liveness Detection
Scanners now verify that the biometric input comes from a living person, not a photo or mold.
For example, facial recognition might check for blinking or blood flow beneath the skin.
B. Revocable Biometrics
Some systems convert biometric data into an encrypted, revocable format that can be reissued if compromised.
C. Multi-Sample & Multimodal Systems
Combining multiple biometric identifiers — like face + fingerprint — increases accuracy and security.
D. Local Encryption
Devices like iPhones store biometric data locally instead of cloud servers, minimizing data exposure.
E. AI Integration
Machine learning enhances biometric accuracy by continuously learning from small changes in appearance, such as aging or lighting differences.
Two-Factor Authentication with Biometrics
Even though biometrics are secure, relying on them alone isn’t foolproof.
The best security practice is to use biometrics as part of multi-factor authentication (MFA).
MFA involves combining:
- Something you are (biometrics)
- Something you have (security token, smartphone)
- Something you know (password or PIN)
Example: Using Face ID to unlock your phone, then entering a PIN or OTP for financial transactions.
This layered approach reduces the chances of unauthorized access, especially for online services and IoT devices.
Ethical and Legal Considerations
As biometrics become widespread, ethical and legal questions have also emerged.
Data Ownership
Who owns your biometric data — you or the company storing it?
Consent
Users must have the right to know when and how their biometric data is being collected.
Regulations
Laws like the GDPR (Europe) and BIPA (U.S.) regulate how organizations collect, store, and use biometric information.
Surveillance Concerns
Cities like London, New York, and Beijing are increasingly linking CCTV footage with facial recognition databases, sparking debates on personal freedom and privacy.
The key challenge lies in balancing public safety with personal privacy.
The Future of Biometrics in Cybersecurity
The future of biometric security looks incredibly promising, thanks to the rise of artificial intelligence and advanced sensors.
Trends to Watch:
- AI-powered adaptive authentication: Systems that continuously learn and adjust to user behavior.
- Integration with blockchain: Creating tamper-proof, decentralized biometric databases.
- Next-generation identifiers: Brainwave patterns, heartbeat signatures, or even scent-based recognition.
- Passwordless authentication: Replacing passwords entirely with biometric access.
As cybersecurity threats evolve, biometrics will remain at the heart of identity verification systems worldwide.
How to Protect Your Biometric Identity
Here are practical steps individuals can take to safeguard their biometric data:
- Use trusted devices that store biometric data locally, not on cloud servers.
- Enable two-factor authentication for critical accounts.
- Avoid unnecessary biometric sharing with third-party apps or services.
- Keep software updated to protect against vulnerabilities.
- Review privacy settings regularly to control how your data is used.
Conclusion
Biometrics has redefined how we think about identity and security. By combining biological uniqueness with digital precision, biometric authentication delivers convenience, speed, and security like never before.
However, no technology is flawless. The permanence of biometric data, combined with privacy concerns, calls for careful implementation and robust safeguards.
Ultimately, the future of cybersecurity lies not in choosing between passwords and biometrics — but in combining them intelligently.
Biometrics, when paired with encryption and multi-factor authentication, will form the foundation of secure digital identity in the coming decades.
FAQs
What is the full meaning of biometrics?
Biometrics refers to the measurement and statistical analysis of a person’s unique physical and behavioral characteristics used for identification or authentication.
How is biometrics used in security?
It’s used for identity verification in smartphones, offices, banks, airports, and government databases — replacing or supplementing passwords with unique biological traits.
What are some common types of biometrics?
Fingerprint, facial recognition, iris scanning, voice recognition, and behavioral biometrics like typing rhythm or gait.
Can biometrics be hacked?
While difficult, it’s possible through spoofing or database breaches. That’s why modern systems use encryption, liveness detection, and multi-factor authentication.
Is biometric data safe?
It’s generally secure when stored locally on a device. However, if stored in centralized databases without strong encryption, it can be vulnerable to cyberattacks.
Debabrata Behera is a passionate blogger who writes about digital trends, personal growth, and practical insights, helping readers stay informed, inspired, and ready to achieve success in life.




