Summary
In today’s digital-first world, passwords, PINs, and access cards are no longer enough to ensure security. With the rapid rise of cyber threats, identity theft, and online fraud, the need for a more reliable and convenient authentication method has become critical. Enter biometrics — a cutting-edge technology that uses the unique physical or behavioral traits of individuals to verify their identity.
From unlocking your smartphone with a fingerprint to facial recognition at airport check-ins, biometrics have seamlessly integrated into our daily lives. But how do biometric systems actually work? What processes are involved? And why are they becoming the cornerstone of modern security?
This comprehensive guide dives deep into what biometrics are, how biometric processes function, and how this technology is revolutionizing industries worldwide.
The word biometrics comes from the Greek words “bio” (life) and “metric” (measure). Quite literally, it means measuring life. Biometrics refers to the automated recognition of individuals based on their unique biological or behavioral characteristics.
In simple terms, it’s a way of saying, “You are who you say you are” — without needing a password, ID card, or key.
Biometrics are everywhere today. They power smartphone security, border control, online banking, healthcare systems, and even employee attendance tracking. Unlike passwords, which can be guessed or stolen, biometric traits are inherent to you — making them far more secure and convenient.
Fun Fact
The idea of using fingerprints for identification isn’t new! In fact, fingerprints were first used in 1858 by Sir William Herschel in India for contract authentication — over 150 years before smartphones made it mainstream!
What Are Biometrics?
Biometrics are measurable physical or behavioral characteristics used to identify or verify an individual’s identity. These characteristics are unique, universal, and permanent — meaning they can’t be easily forged or shared.
For example:
- Your fingerprint pattern is unique — even identical twins don’t share the same one.
- Your voice and facial structure have distinctive features that remain stable over time.
- Your iris has patterns that are as unique as snowflakes — no two are alike.
Types of Biometrics
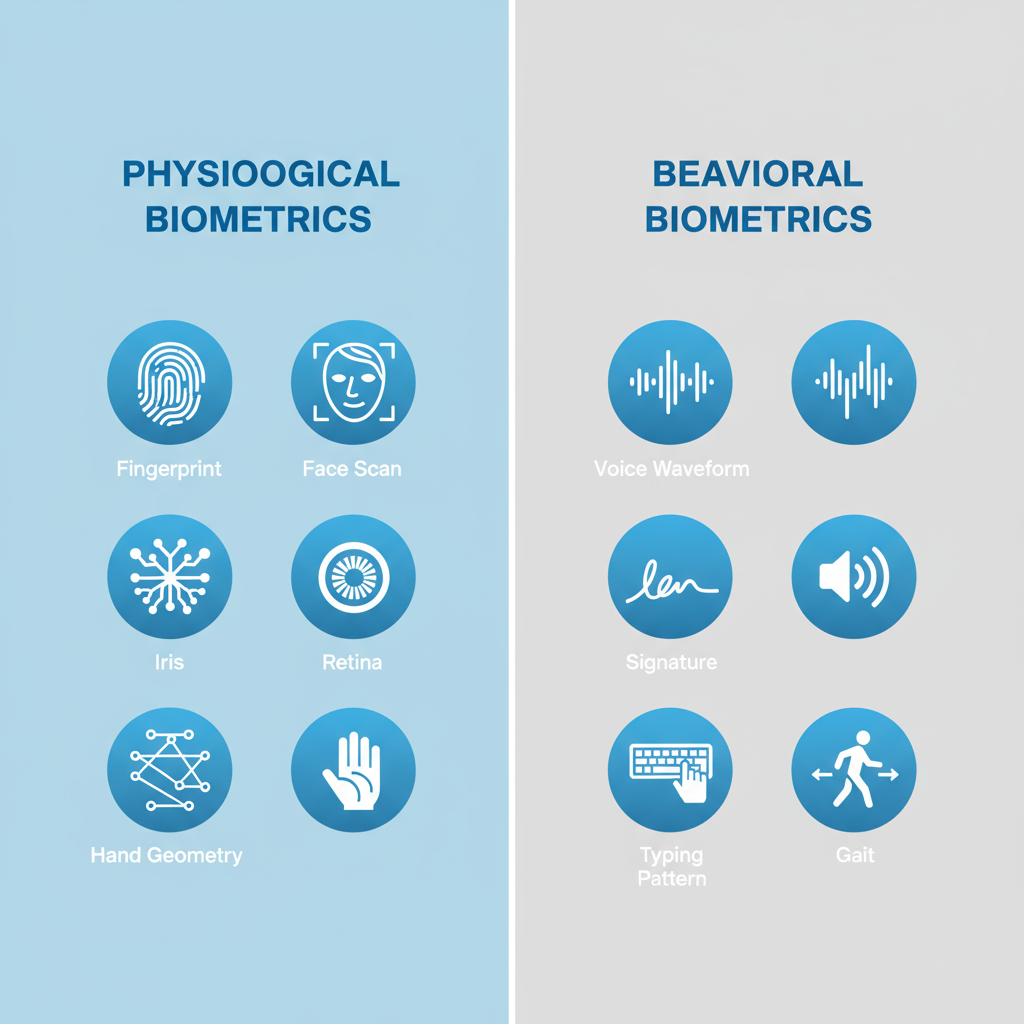
Biometrics are generally classified into two main categories:
A. Physiological Biometrics
These are based on physical attributes of the human body.
Common examples include:
- Fingerprint Recognition: The most widely used biometric method, analyzing ridge patterns on fingers.
- Facial Recognition: Identifies unique facial structures using distance between eyes, nose, and jawline.
- Iris Recognition: Scans the colored ring of the eye to map intricate patterns.
- Retina Scanning: Captures unique blood vessel patterns at the back of the eye.
- DNA Matching: Used in forensics, comparing genetic sequences for identity verification.
- Hand Geometry: Measures the shape and size of a person’s hand.
B. Behavioral Biometrics
These are based on how people perform certain actions.
Common examples include:
- Voice Recognition: Identifies individuals based on speech patterns, pitch, and tone.
- Signature Analysis: Evaluates stroke speed, pressure, and rhythm while signing.
- Typing Pattern Recognition: Detects typing rhythm and keystroke speed.
- Gait Analysis: Recognizes people by the way they walk.
Pro Tip
When selecting a biometric method for your business, consider three factors — accuracy, speed, and user comfort. For example, fingerprints are fast and easy, while iris scans are more accurate but slightly less user-friendly.
How Do Biometric Systems Work?
Biometric systems don’t just recognize people by “looking” at their faces or fingerprints. They follow a structured, multi-step process that involves capturing, processing, and comparing biometric data.
Let’s break down the biometric process into five key stages:
Step 1: Data Capture
In this initial stage, the biometric system collects data from an individual using a sensor or scanner.
Examples:
- A camera captures a face or iris image.
- A fingerprint scanner records fingerprint ridges.
- A microphone captures voice data.
This raw data forms the foundation for later comparison. The quality of captured data significantly affects accuracy — a blurry face image or smudged fingerprint can lead to errors.
Step 2: Feature Extraction
After data collection, the system converts raw data into digital templates. It identifies distinct features such as:
- Minutiae points on fingerprints
- Eye distances in facial recognition
- Pitch frequency in voice analysis
These extracted patterns are encoded into mathematical representations. The goal is to create a unique biometric template that represents each person digitally.
Step 3: Data Storage
Once extracted, the biometric template is securely stored in a database or device.
There are two storage methods:
- Centralized Database: Common in government or large enterprise systems.
- Local Storage: Found in devices like smartphones, where your biometric data is stored securely on your phone’s chip.
Importantly, biometric systems never store images — only encrypted templates that cannot be reverse-engineered into the original image.
Step 4: Comparison (Matching)
When a user tries to authenticate, the system captures a new sample and compares it to stored templates.
There are two matching modes:
- Verification (1:1): Confirms a person’s claimed identity (e.g., unlocking your phone).
- Identification (1:N): Searches for a person’s identity within a database (e.g., airport security).
Matching algorithms calculate a similarity score, and if the score exceeds a certain threshold, access is granted.
Step 5: Decision
Finally, the system determines whether the match is successful.
- If yes, the user is authenticated.
- If no, access is denied or further verification is required.
This decision-making process is almost instantaneous, usually taking less than a second in modern systems.
Fun Fact:
Your fingerprint sensor doesn’t actually store your fingerprint image — it stores a mathematical model of your ridges and patterns. Even if hackers stole it, they couldn’t recreate your actual fingerprint!
The Benefits of Biometric Technology

Biometrics offer a range of advantages over traditional authentication methods:
Enhanced Security
Biometric traits are unique and difficult to fake or steal. Unlike passwords, which can be guessed or hacked, biometrics tie authentication directly to a person’s physical identity.
Convenience and Speed
You don’t have to remember anything — no passwords, no ID cards. A simple scan or selfie grants access in seconds.
Accuracy and Reliability
Modern biometric algorithms are highly accurate, with error rates below 0.1% in many systems. Continuous updates and AI integration make them even smarter over time.
Cost-Effectiveness
While initial setup can be expensive, biometrics reduce long-term costs by eliminating password resets, card replacements, and manual verification processes.
Fraud Prevention
By linking identities to unique physical or behavioral characteristics, biometrics minimize fraud risks in banking, travel, and online services.
Pro Tip
Combine biometric authentication with multi-factor verification (like OTP or PIN) for the strongest security defense. This adds an extra layer of protection without hurting convenience.
Challenges and Limitations of Biometrics
While biometrics offer impressive advantages, they’re not without challenges:
Privacy Concerns
Since biometrics involve personal biological data, ensuring data protection and user consent is critical. Regulations like GDPR and India’s DPDP Act govern biometric data usage strictly.
Spoofing and Presentation Attacks
Hackers can attempt to trick systems using photos, masks, or deepfakes. To combat this, liveness detection (especially passive liveness) has become a must-have layer in modern systems.
Environmental Limitations
Poor lighting, dirt on fingers, or background noise can affect accuracy. Systems must adapt to real-world conditions.
Ethical and Inclusion Issues
Some facial recognition systems have shown algorithmic bias, performing less accurately on certain skin tones or genders. Developers are now focusing on fairness and inclusivity in AI models.
Real-World Applications of Biometrics
Biometric technology is shaping nearly every industry. Here’s where it’s making the biggest impact:
Banking and Fintech
- Facial and fingerprint authentication for secure mobile banking.
- Voice recognition for phone banking.
- Preventing identity fraud in account openings.
Healthcare
- Patient identification and record access.
- Secure telemedicine consultations.
- Prescription verification and drug dispensing systems.
Border Control and Travel
- Automated immigration gates using facial recognition.
- Contactless travel verification.
- Faster check-ins and boarding.
Workforce Management
- Biometric attendance systems.
- Access control in restricted areas.
- Employee time tracking in hybrid work environments.
Law Enforcement
- Criminal identification using fingerprint and facial databases.
- Missing person identification.
- Border surveillance and public safety monitoring.
Fun Fact
Airports like Dubai and Singapore now allow passengers to board flights using just facial recognition — no passport, no boarding pass, no lines!
The Future of Biometrics
The future of biometrics lies in continuous authentication — verifying identity constantly, not just once. Technologies like gait analysis, heartbeat recognition, and behavioral analytics will make identity verification invisible yet more secure.
We’re also moving toward multimodal biometrics, combining two or more traits (like face + voice) for even higher accuracy.
AI and machine learning will continue to enhance biometric reliability, while privacy-preserving technologies like on-device encryption and federated learning will ensure user data stays safe.
Conclusion
Biometrics are redefining the way we interact with technology. What once seemed futuristic — unlocking your phone with your face or verifying identity with a voice command — is now an everyday reality.
With the right balance of innovation, ethics, and privacy, biometrics promise a world where security becomes seamless, personal, and effortless.
Whether you’re a business leader, developer, or user — understanding biometrics and their processes is key to navigating this new era of digital identity.
FAQs
What are biometrics in simple terms?
Biometrics are physical or behavioral characteristics — like fingerprints, face, or voice — used to identify and authenticate individuals.
How do biometric systems work?
They capture biometric data, extract unique features, store them securely, and match them during verification or identification.
What are the main types of biometrics?
Physiological (fingerprint, iris, face) and behavioral (voice, signature, typing pattern).
Are biometrics completely secure?
While highly secure, they should be combined with encryption and liveness detection to prevent spoofing.
Where are biometrics used today?
In banking, healthcare, law enforcement, border control, and workforce management.
Do biometrics invade privacy?
Not if implemented correctly. Ethical biometrics follow data protection laws and store encrypted templates, not actual images.
Debabrata Behera is a passionate blogger who writes about digital trends, personal growth, and practical insights, helping readers stay informed, inspired, and ready to achieve success in life.