Summary
In the digital era, identity is everything — and securing it has never been more important. As passwords continue to fail in the face of cyber threats, businesses and individuals are turning to biometrics for a more reliable form of authentication. Among these, voice authentication software has emerged as a powerful, contactless, and user-friendly method of verifying identity.
This article explores how voice authentication works, the technology behind it, its advantages and limitations, and why it’s becoming a cornerstone of modern cybersecurity.
Imagine unlocking your phone, logging into your bank, or authorizing a payment — all by simply speaking a phrase. What sounds futuristic is already here.
Voice authentication software uses a person’s unique vocal characteristics to confirm identity. As part of the broader field of biometric authentication, it provides a convenient and secure alternative to passwords, tokens, or PINs.
Unlike traditional credentials that can be forgotten, stolen, or shared, your voice is inherently yours. The pandemic also accelerated the need for contactless authentication, making voice biometrics even more relevant in today’s environment.
But before diving into how it works, let’s understand what voice authentication really means.
What Is Voice Authentication?
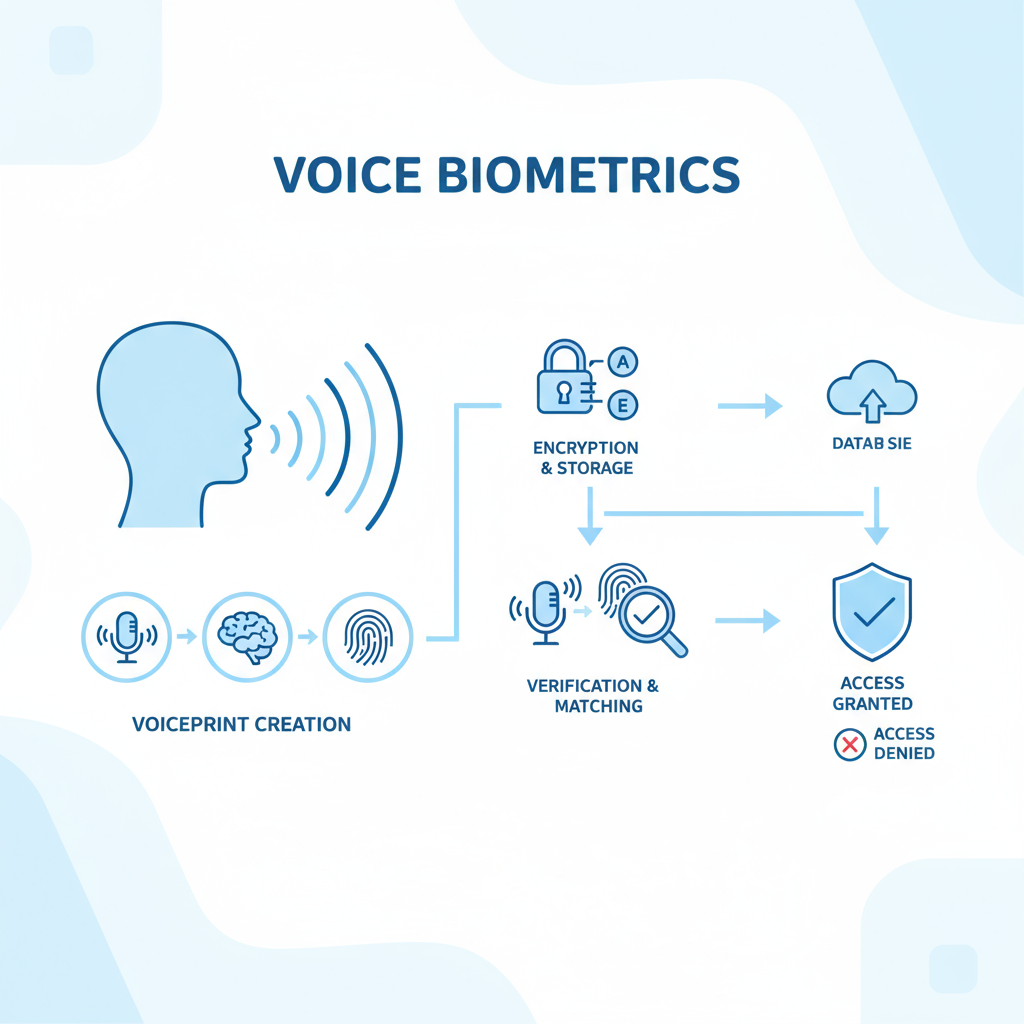
Voice authentication (also called speaker recognition) is a biometric process that identifies or verifies a person based on their unique voice patterns.
Every individual’s voice has distinctive acoustic features influenced by the shape of their vocal tract, mouth, nasal cavity, and even behavioral traits like accent, pitch, and tone. These characteristics form a voiceprint, similar to how fingerprints or iris scans represent physical identifiers.
When you enroll in a voice authentication system, your speech sample is recorded and analyzed to create a digital model — your “voice identity.” Later, when you attempt to log in or perform an action, the system compares your live voice sample against the stored voiceprint to verify authenticity.
Voice Recognition vs Speech Recognition
A common misconception is that voice recognition and speech recognition are the same. They are related but serve different purposes:
- Speech recognition focuses on what you say — converting spoken words into text or commands (like Siri or Alexa).
- Voice recognition, on the other hand, focuses on who is speaking — analyzing vocal patterns to confirm identity.
In other words, speech recognition understands content, while voice authentication software verifies the speaker.
Approaches to Voice Authentication
There are two primary types of voice authentication methods:
A. Text-Dependent Voice Authentication
In text-dependent systems, users must say a specific phrase or passcode during enrollment and authentication.
Examples:
- Static phrases like “My voice is my password.”
- Dynamic phrases, where a system generates random words or numbers each time (for higher security).
Pros:
- High accuracy and easy to implement.
- Suitable for secure environments like banking and contact centers.
Cons:
- Limited flexibility — the user must remember or repeat specific phrases.
B. Text-Independent Voice Authentication
In text-independent systems, users can say anything — the system identifies them based on voice patterns alone.
Pros:
- More flexible and user-friendly.
- Works well in natural conversation (like customer service calls).
Cons:
- Requires more sophisticated algorithms and may have slightly lower accuracy than text-dependent systems in noisy environments.
Both approaches have value, and modern voice authentication software often combines them for stronger, context-aware security.
How Voice Authentication Works
The process behind voice authentication involves several precise steps and technologies:
1. Enrollment
The system records a user’s voice and analyzes its unique acoustic features — pitch, tone, rhythm, and pronunciation.
This data is processed to create a mathematical model or voiceprint, which is securely stored in an encrypted format.
2. Verification
When the user later tries to authenticate, the system captures a new voice sample and compares it with the stored template.
If the similarity score exceeds a certain threshold, the identity is confirmed.
3. Matching
The software uses algorithms that analyze:
- Physiological traits: shape of the vocal cords and resonance chambers.
- Behavioral traits: speaking style, accent, and intonation patterns.
This combination makes the voiceprint unique and difficult to forge.
The Importance of Voice Liveness Detection
While voice biometrics is secure, it’s not entirely immune to spoofing attempts, such as replayed recordings or AI-generated voice deepfakes.
That’s where voice liveness detection — also known as presentation attack detection (PAD) — plays a vital role.
What Is Voice Liveness Detection?
Liveness detection ensures that the voice sample comes from a real, live human and not from a recorded or synthetic source.
How It Works:
- The system challenges the user to speak random phrases or numbers.
- The microphone analyzes real-time acoustic variations such as breath, background noise, and natural speech inconsistencies.
- Advanced algorithms identify whether the voice is authentic or artificially produced.
This adds an extra layer of defense against deepfake and spoofing attacks, which are increasingly sophisticated.
Accuracy and Environmental Challenges
Every biometric system must balance accuracy and usability.
For voice authentication software, accuracy is typically measured by:
- FAR (False Acceptance Rate): How often unauthorized users are accepted.
- FRR (False Rejection Rate): How often genuine users are rejected.
- EER (Equal Error Rate): The point where both rates are equal — lower is better.
However, external factors can affect accuracy:
- Background noise and poor microphone quality.
- Voice changes due to illness, stress, or aging.
- Environmental acoustics and echo.
Modern systems use AI and deep learning to continuously adapt and improve performance, even with changing voice conditions.
Security Risks and Limitations
While voice biometrics is one of the most user-friendly forms of authentication, it has its own set of challenges:
1. Spoofing Risks
Attackers can use recorded or synthesized voices to impersonate users. Without liveness detection, these attacks can sometimes succeed.
2. Data Breaches
If stored voiceprints are compromised, they cannot be changed like passwords. Therefore, encryption and local storage are critical.
3. Accuracy Variations
No authentication method is perfect. Factors like colds, sore throats, or microphone issues can affect performance.
4. Privacy Concerns
Users must be informed about how their biometric data is collected, used, and stored to comply with global privacy laws.
To mitigate these, multi-factor authentication (MFA) is often recommended — combining voice with another factor such as a PIN, OTP, or device token.
Privacy, Compliance, and Ethical Considerations
Biometric systems, including voice authentication, handle sensitive personal data — making privacy a top priority.
Regulatory Guidelines Include:
- GDPR (General Data Protection Regulation): Enforces data protection and explicit consent before collecting biometric information.
- BIPA (Biometric Information Privacy Act): Requires transparency in biometric data collection and storage.
Organizations must ensure:
- Voiceprints are encrypted and non-reversible.
- Users consent to data use.
- Data is deleted after purpose completion.
Privacy by design should be built into every stage of voice authentication deployment.
Key Use Cases of Voice Authentication Software
1. Banking & Financial Services
Banks use voice biometrics for account access, customer support, and fraud prevention.
Customers can verify identity by speaking a passphrase, reducing reliance on PINs or security questions.
2. Contact Centers
Voice authentication replaces long, frustrating security questions during customer service calls.
It identifies callers in seconds, improving customer experience and reducing handling time.
3. Smart Devices & IoT
Voice recognition enables secure, hands-free access in smart homes, vehicles, and virtual assistants.
4. Workforce Authentication
Employees can log in to systems or time-track without touching devices — ideal for remote work and hygiene-sensitive environments.
5. Healthcare
Medical staff can access patient records using voice verification, ensuring data security without slowing down workflows.
Advantages of Voice Authentication Software
- Contactless and Hygienic: Ideal in a post-pandemic world.
- High Accessibility: Every smartphone has a microphone — no special hardware required.
- User Convenience: No need to remember passwords or carry access cards.
- Cost-Effective: Easy integration with existing systems and devices.
- Scalable: Works across mobile apps, IVR systems, and enterprise platforms.
Disadvantages and Challenges
While voice authentication has numerous benefits, there are a few challenges:
- Not ideal in noisy environments or for users with speech impairments.
- Requires consistent voice quality for accuracy.
- Must rely on advanced anti-spoofing algorithms to prevent misuse.
- Privacy concerns around data collection and consent.
These limitations can be mitigated through multi-modal biometrics — combining voice with facial or fingerprint recognition for higher assurance.
Implementation and Best Practices
For a successful voice authentication deployment, organizations should follow these steps:
- Define Use Case: Identify where voice biometrics fits — customer login, employee access, or call center authentication.
- Choose Authentication Mode: Text-dependent for high security or text-independent for convenience.
- Integrate Liveness Detection: Essential for preventing spoofing and replay attacks.
- Ensure Privacy Compliance: Follow GDPR, BIPA, and regional laws.
- Provide Fallback Options: Offer PIN or OTP for users unable to authenticate via voice.
- Regularly Update Algorithms: Keep up with emerging deepfake and spoofing technologies.
Pro tip: Always combine biometrics with other authentication factors for optimal protection.
The Future of Voice Authentication in Cybersecurity
Voice authentication is evolving rapidly alongside artificial intelligence and machine learning.
Also Read:How Biometrics Enhance Multifactor Authentication
Emerging Trends:
- AI-powered adaptive models: Continuously learn from subtle changes in a user’s voice.
- Multimodal authentication: Combining voice, face, and behavioral biometrics for higher accuracy.
- Integration with IoT: Voice-based access for smart homes, vehicles, and wearables.
- Deepfake detection: New algorithms can detect synthesized or cloned voices with high precision.
- Passwordless systems: Replacing passwords entirely with biometrics for seamless, secure login.
In the coming years, voice biometrics will not just complement other security systems — it will redefine the future of digital identity verification.
FAQs
What is voice authentication software?
Voice authentication software uses biometric technology to verify a user’s identity based on their unique voice characteristics, such as pitch, tone, and pronunciation patterns.
How secure is voice recognition?
When combined with liveness detection and encryption, voice recognition is highly secure. It’s harder to spoof than passwords, though not entirely immune to deepfakes.
What’s the difference between text-dependent and text-independent voice authentication?
Text-dependent systems require a specific phrase, while text-independent systems can verify identity from any spoken words.
Can environmental noise affect voice authentication?
Yes. Background noise can reduce accuracy, so high-quality microphones and noise-canceling algorithms are essential.
Is voice data stored on servers?
It depends on implementation. For higher privacy, many systems store voiceprints locally on the device instead of cloud servers.
Can I use voice biometrics as part of MFA?
Absolutely. Voice can be one factor in multi-factor authentication, combined with passwords, devices, or tokens for enhanced security.
What happens if my voice changes due to illness?
Most advanced systems allow for re-enrollment or adapt to minor voice variations caused by illness or aging.
Is voice authentication suitable for businesses?
Yes. It’s widely used in banking, telecom, customer service, and workforce management due to its speed, convenience, and security.
Conclusion
Voice authentication software represents a major step forward in the evolution of biometric security. It offers an ideal blend of convenience, cost-efficiency, and contactless verification — making it perfect for modern digital systems.
However, as with all biometrics, it’s not entirely foolproof. To ensure maximum protection, voice authentication should be used alongside liveness detection and multi-factor authentication strategies.
Debabrata Behera is a passionate blogger who writes about digital trends, personal growth, and practical insights, helping readers stay informed, inspired, and ready to achieve success in life.




